In today’s digital-first world, cybersecurity is no longer optional — it’s foundational. DSi’s Cyber Solutions protect your infrastructure, data, and workforce from evolving threats, ensuring business continuity and compliance across hybrid and cloud environments.
Cyber Solutions
- Protect What Matters Most.
- Stay Secure, Stay Ahead
- Mitigate Ransomware Attack Vectors
- Protect Your Digital Assets with Confidence
- Stay Ahead of Evolving Threats with Expert Cybersecurity.
DSi's Cyber Assessment is a unique service offering and can also include monthly and quarterly cyber risk assessments across your infrastructure and directory services for ongoing cyber support.
Our Approach
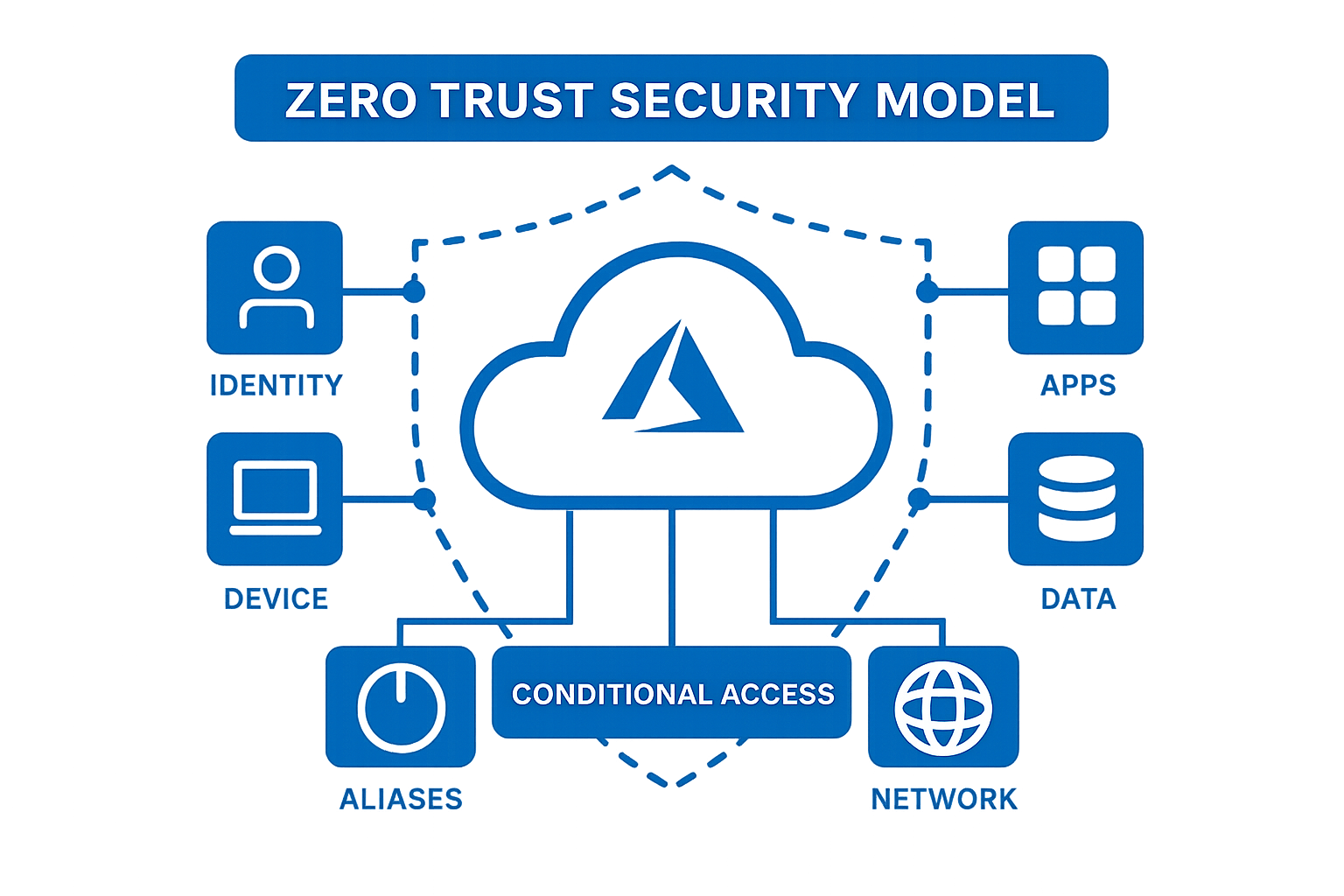
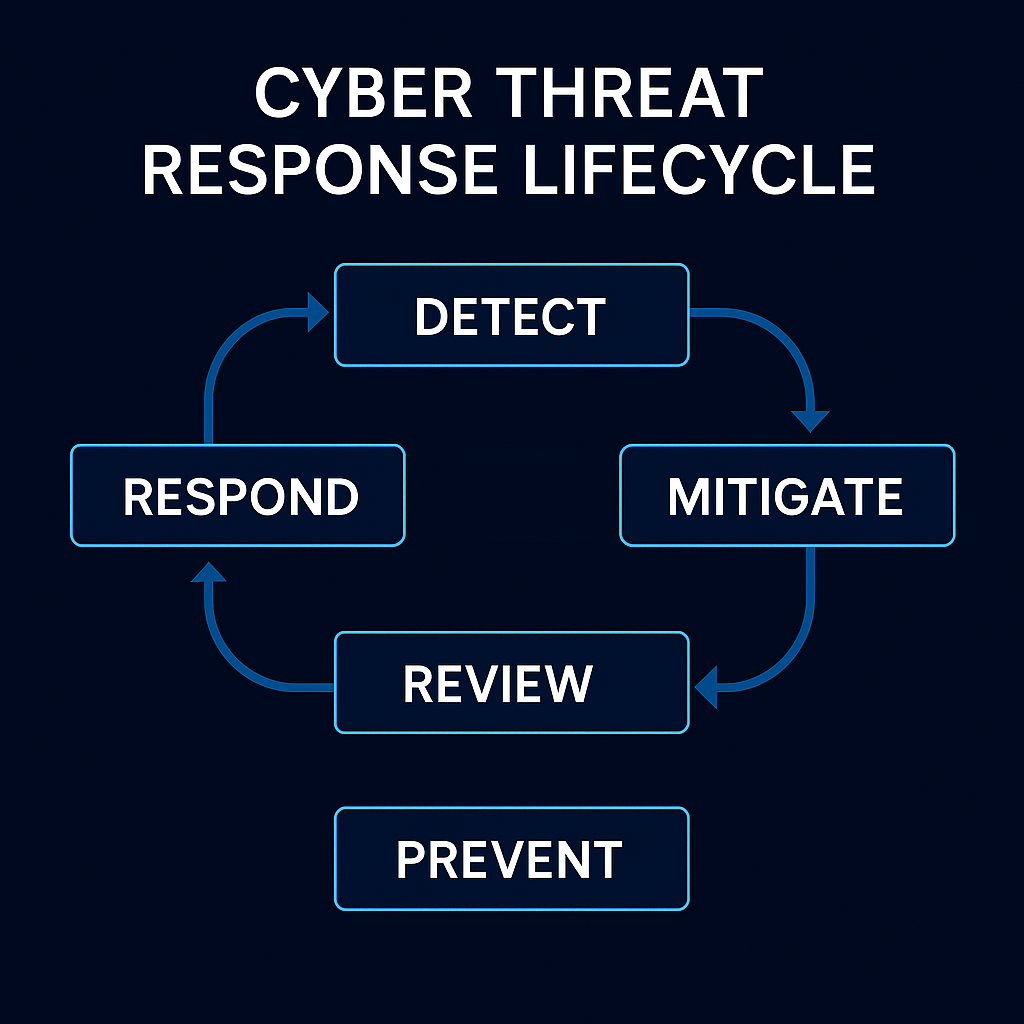
DSi takes a zero-trust, defence-in-depth approach to cybersecurity. We tier identity access, harden infrastructure, and deploy continuous monitoring using tools like Microsoft Sentinel and Defender. We don’t just respond to threats — we help you predict and prevent them.
Through strategic monthly or quarterly security assessments, we continuously evaluate your infrastructure against evolving risks. Whether you’re running on-prem systems, Azure, Microsoft 365, or a hybrid blend — we bring structure, visibility, and resilience to your digital defences.
In an era where digital threats are evolving at an unprecedented rate, safeguarding your organization’s assets is critical. Our Cyber Solutions team specialises in identity access management, ransomware mitigation, and comprehensive security assessments. We protect your infrastructure and cloud resources through robust security configurations, regular audits, and advanced threat detection and response strategies.

Business Challenges We Solve
- Mitigating risks associated with hybrid Azure AD users
- Enhancing security architecture and hardening measures
- Improving identity and access management practices
- Increasing visibility and monitoring capabilities
- Safeguarding sensitive data and ensuring disaster recovery readiness
- Reducing risks associated with cloud and hybrid models
Business Outcomes
- Reduced cyber risk and stronger resilience to ransomware
- Confident compliance with international security standards
- Clear audit trails and incident response playbooks
- Secure user access across hybrid and cloud environments
- Peace of mind for leadership, IT teams, and stakeholders
Create and target content dynamically
- Hybrid & Cloud Infrastructure Hardening and Ransomware Mitigation
- Conditional Access & Device Compliance Frameworks
- Security Assessments & Gap Analysis (ISO, ANSII, CIS)
- Active Directory Design, Tiering, and Remediation
- Identity Management and Ransomware Mitigation
- Advanced Threat Detection with Microsoft Sentinel and Defender
- Microsoft Azure and Entra ID security policy management and privileged access design, deployment, and remediation.
- On-Premises Lightweight Directory Services and Active Directory Services hardening using ANSII and ISO27001 security practices.
